Statement Best Describes Same Origin Policy
If both web page origin from same domain and web server then browser can access second page data through first page script and the feature named as Same-Origin Policy in terms of web application security model. Reducing the need for CloudFront to go back to the origin server and improving.
If you include another domains scripts under your own site then you are giving full access to your origin to that domain.

. It helps isolate potentially malicious documents reducing possible attack vectors. The X Men Logo. What Same-Origin Policy is.
The same origin policy is an important concept in the web application information security domain. Which Statement Best Describes Same-origin Policy. For example it prevents a malicious website on the Internet from running JS in a browser to read data from a third-party webmail.
By Ra_Linda917 26 Apr 2022 Post a Comment Using SAML Security Assertion Markup Language 20 you can give your federated users single sign-on SSO access to the AWS Men The wallpaper X. Definition of an origin Two pages have the same origin if the protocol port if one is specified and host are the same for both pages. Same origin policy is a common feature found in most client scripting languages and their created applications that relyon HTTP cached cookies for user authentication access control and other security related tasks.
The same-origin policy is a critical security mechanism that restricts how a document or script loaded from one origin can interact with a resource from another origin. The X Men Logo. SOP refers to a mechanism that governs the ability for JavaScript and other scripting languages to access DOM properties and methods across domains.
If you look in the JavaScript console youll see something like this. According to this policy only resources of the same origin can access the data on the second web page. Follow this answer to receive notifications.
In computing the same-origin policy sometimes abbreviated as SOP is an important concept in the web application security model. Software exploit that can only be used for a. Which of the following statements best describes the origin.
By Ra_Linda917 26 Apr 2022 Post a Comment. Same-Origin Policy defines the rules for the browser to control access to the data between two web pages. Reflected non-persistent XSS is the most common type of cross-site scripting.
Without SOP any web page would be able to access the DOM of other pages. The same-origin policy is a critical security mechanism that restricts how a document or script loaded by one origin can interact with a resource from another origin. Software exploit identified during day zero of vendor testing b.
The term Same-Origin Policy SOP is used to denote a complex set of ruleswhich governsthe interaction of dif- ferent Web Origins within a web application. Same origin policy is designed to ensure that separate website scripts and applications do not interfere with the access control credentials of other websites. Same Origin Policy SOP is an important concept in the web application security model.
With all three types of cross-site scripting XSS vulnerability occurs if data from either the Web page or the user fails to include what. Basically content received from one website is allowed to read and modify other content received from the same site but is not allowed to access content received from other sites. Which statement is true in relation to the three general types of cross-site scripting XSS.
This would let it access potentially sensitive data from another web page as well as perform actions on other web pages without user consent. The same-origin policy is a key mechanism implemented within browsers that is designed to keep content that came from different origins from interfering with each other. Here you have an excellent description of different types of SOP.
The point contains positive and positive integers. Same Origin Policy The same-origin policy restricts how a document or script loaded from one origin can interact with a resource from another origin. It helps isolate potentially malicious documents reducing possible attack vectors.
The point contains positive and negative integers. What is Same Origin Policy. Only GET requests are subject to the same - origin policy.
Question 15 Question text Select the statement that best describes what a zero-day exploit is. Availability Zones in the same region are connected through low-latency links 2 or more AZs Please fill in the gaps. A subset of these SOP rules controls the interaction between the host document and an embedded documentand this subset is the target of our research SOP-DOM.
Same-Origin Policy an advanced concept on Web App Security Model introduced by Netscape Navigator 2 in 1995. The same-origin policy is a critical security mechanism that restricts how a document or script loaded from one origin can interact with a resource from another origin. The reason behind this behavior is security.
The point contains negative and negative integers. Answered Sep 24 2010 at 306. An origin is defined as a combination of URI scheme host name and port number.
Each DC with redundant power networking and connectivity housed in seperate facilities. In this policy a web browser allows scripts contained in a first web page A to access dataresources in a second web page B however. Which Statement Best Describes Same-origin Policy.
It is a critical security mechanism for isolating potentially malicious documents. SOP is also used to prevent cross-domain AJAX requests. By Ra_Linda917 26 Apr 2022 Post a Comment.
The SOP does not stop a cross-domain AJAX request from being made - it simply stops it from being read. Same-Origin Policy SOP is a rule enforced by web browsers which controls access to data between websites and web applications. The Same-Origin Policy helps browsers to prevent malicious scripts on the first page to access sensitive data on the.
As per this policy it permits scripts running on pages originating from the same site which can be a combination of the following. Which statement best describes an IAM policy. Show activity on this post.
It helps isolate potentially malicious documents reducing possible attack vectors. Under the policy a web browser permits scripts contained in a first web page to access data in a second web page but only if both web pages have the same origin. By Ra_Linda917 26 Apr 2022 Post a Comment Using SAML Security Assertion Markup Language 20 you can give your federated users single sign-on SSO access to the AWS Men The wallpaper X.
Developer Program Policy Play Console Help

Agile Retrospective Yodiz Agile Scrum Lean Kanban Kaizen Lean Kanban Problem Solving

Negative Prefixes In Im Il Ir Un Dis Prefixes Prefix Worksheet Root Words Activities
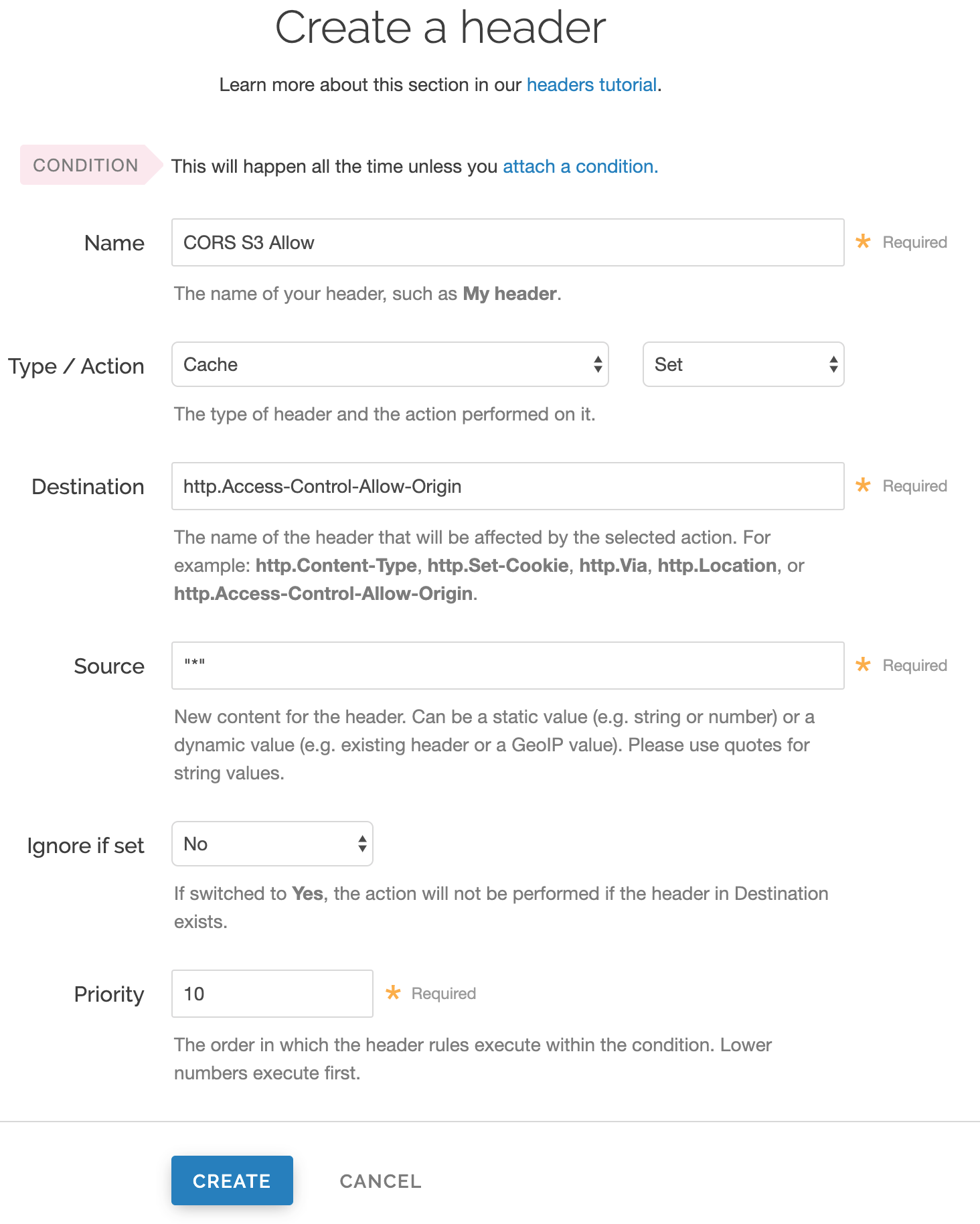
Enabling Cross Origin Resource Sharing Cors Fastly Help Guides
Comments
Post a Comment